By Dr. Karl So, Doctorate of Business Administration
Following the WFH challenge to share or transfer large files, the next question is how to manage security when you do that at home, and setting up network security is never easy for ordinary office persons.
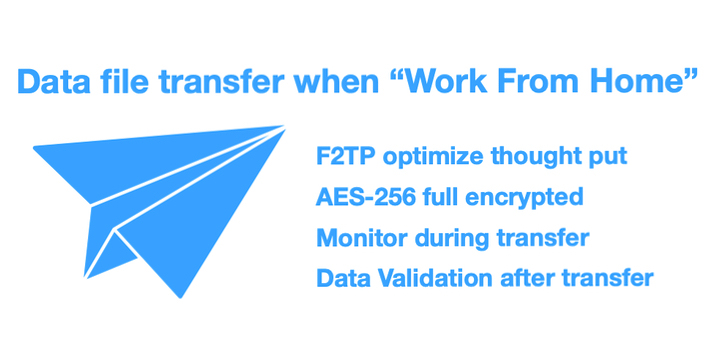
The most common way is using FTP, or File Transfer Protocol is one of the ways to transfer data files between computers and servers. It was developed in the early 1970s, files were small, internet speed was slow. But comparing today’s internet usage, mobile phone CPU as powerful as a desktop computer, media creation is faster than ever, data files are getting bigger and bigger. Will a 50yrs old protocol able to handle that? And the security has been changing over time, sharing a file over the public internet is always at your own risk.
The business works by creating value in the market and generate profit. Since the digital revolution, the industry needs to incorporate information technology to meet their goals. The security has come out as the most devastating challenges for modern business. Unfortunately, the SMEs are more on target as they have meager resources as well as bucks in hand to invest. In the early days, physical security was enough for any business, whereas now, the organization boundary has extended virtually to include devices and data, leaving the boundaries of the organization. Threats like ransomware, phishing, identity theft are advancing with time. These are threats like the followings.
Theft Risk
Small offices consist of a handful of people working in collaboration. Hence there is no concept of isolation of personal belongings. Moreover, the idea of BYOD is now common in startups or small businesses. Proper information security policies are also absent. The environment thus becomes very favorable for a malicious person to carry out theft and perform any fraudulent activity. Reports in the US manifest the alarming rise in data theft in small offices. US business has reported the loss by theft, in billions. Consequently, the company has to suffer monetary as well as data and information loss.
Lack of Auditing
In the usual medium available for internet use, there is a limit to identifying and authenticating the users on both sides of the communication. Employees often need a remote communication link for support work. With no access control or authentication mechanism in place, the session can be hijacked by any expert adversary. Using a secure channel enforces the access control and provides metadata about the sender and receiver. This way ensures protection against any phishing or social engineering attempt that often leads to data and identity theft.
Cost Burden
Small businesses have their email set up locally, which is the primary source of communication between employees, partners, and customers. Therefore, the connection needs to be secured through a communication channel that is also under the budget for SMEs. Since the traditional leased lines from ISP are costly and have a humongous upfront fee, beyond the reach of small business. An economically secure channel is the ideal requirement.
These requirements fit well into the F2TP Fast File Transport Protocol solution. With the file transfer service like Cydex, small enterprises can get a secure channel that is much faster than FTP and provide good network-level performance in terms of bandwidth and latency. A feature complimentary with F2TP is end-end security. It offers a complete solution of control servers, monitoring applications, support, and integration with email systems. Cydex Service gives a good level of encryption with AES 256 bit at both session and control layer. The sender and receiver notification allow the parties to stay in sync through status information. The solutions work well with portable devices like mobile and also has email and web support to help the small organizations in their daily routine without trouble. The solution gives much more in much less effort.



















Comment